
iMessage Contact Key Verification is a feature straight out of a spy film

Edgar Cervantes / Android Authority
TL;DR
- Apple has added an advanced security feature to iMessage.
- It’s called iMessage Contact Key Verification and allows users to verify that they are messaging only the people they intend to chat with.
- The feature also alerts users if someone starts eavesdropping on their messages.
Apple’s iMessage is perhaps one of the most popular messaging apps out there. Even though it’s restricted to iOS users and hasn’t let in the Android crowd yet, it offers some of the best chat and security features. End-to-end encryption has been a part of iMessage since the launch of the service, but Apple is making it even more secure with a new feature.
Called iMessage Contact Key Verification, the security feature for Apple’s chat app will allow users to verify that they are messaging only with the people they intend to talk to.
Users who have enabled iMessage Contact Key Verification will receive automatic alerts if an “exceptionally advanced adversary,” such as a state-sponsored attacker, were ever to succeed in breaching cloud servers and eavesdropping on encrypted iMessage conversations.
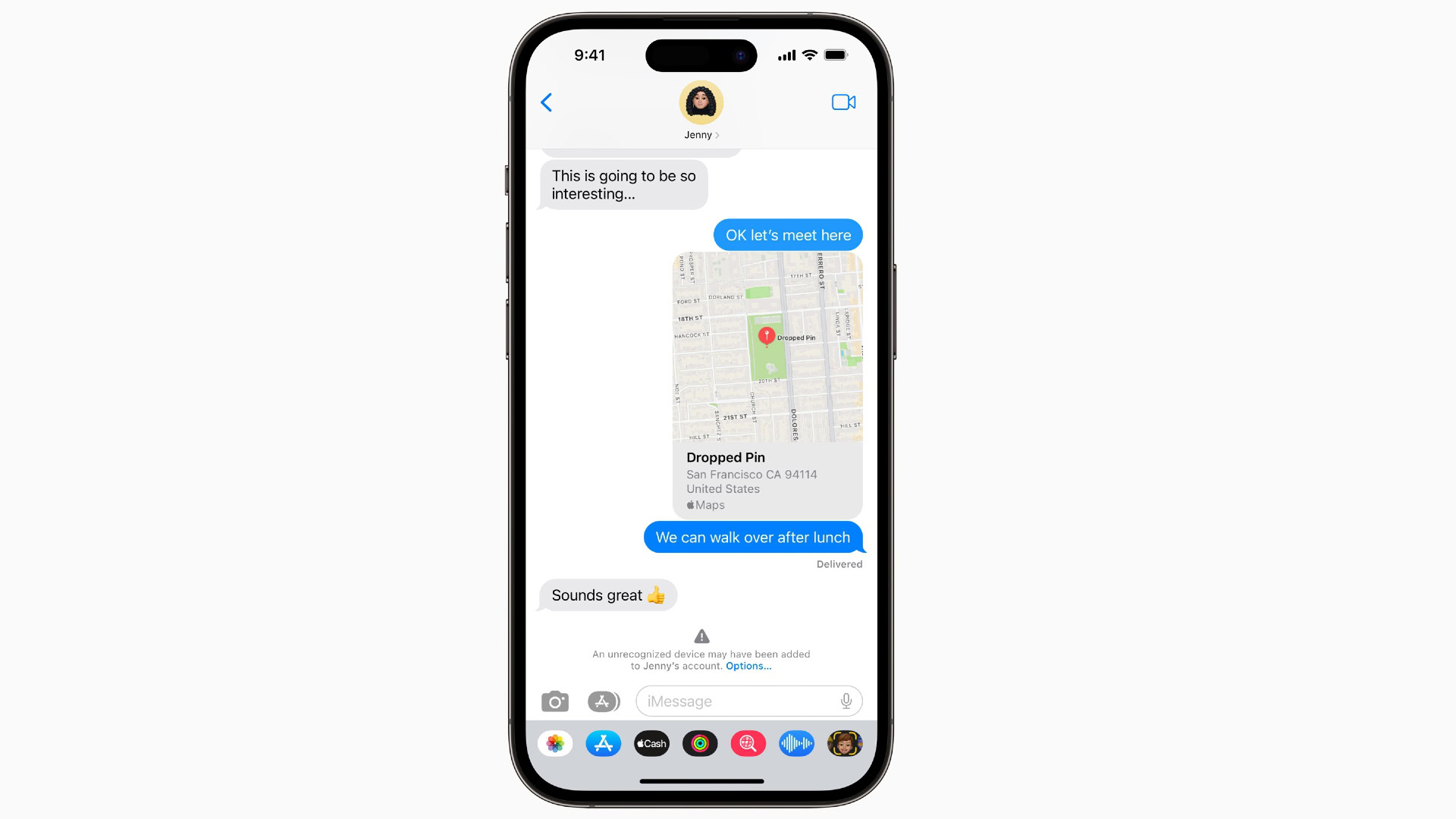
We know what you’re thinking — “This stuff will never happen to me.” You’re probably right. The advanced iMessage security feature may be overkill for regular folks like us, but Apple says it’s meant for “users who face extraordinary digital threats — such as journalists, human rights activists, and members of government.” If you belong to those groups, this might be a crucial feature for you.
Apple didn’t go into a lot of detail about how Contact Key Verification will work when it launches in 2023. However, the company said that users who enable it will be able to compare a Contact Verification Code in person, over FaceTime (which is also end-to-end encrypted), and through another secure call.
